
About Us – IT Security & Cybersecurity Hardware Products
IT Security Hardware & Cybersecurity hardware security about us – products and our solutions.
- Cyber Threat Solutions
- Cyber Protection Solutions
- Industry Solutions
- Smart Mobile POS Systems for Modern Businesses
- Cybersecurity hardware
- Multi-Factor Authentication
- FIDO2 PIN+ Series
- Dual-Port FIDO2 Security Keys
- PIV Devices
- Classic OTP tokens
- PIN+ Bio3
- FIDO2 Keys and Cards
- FIDO2 PIN+ Series
- Multiprofile TOTP Tokens
- TOTPRadius
- UserLock compatible keys
- Dynamic Strong Password
- Duplication Solutions/Replication System
- Classic 2FA / MFA
- Cloud-Based MFA Service
- On-Prem MFA Platform
- Dynamic Strong Password Authentication
- Wi-Fi Authentication
- SMS Based Authentication for Wi-Fi
- Electronic Visit Verification (EVV)
- PIV Devices
- FIDO2 with NFC
- FIDO2 with TOTP
- FIDO2 Cards
- Programmable Tokens
- Software protection hardware dongle key
- MFA for VPN
- MFA for Computer Login
- MFA for Remote Desktop
- MFA for Exchange Emails
- MFA for IIS Websites
- MFA for Cloud Services
- MFA for Office 365
- MFA for NetMotion Mobility
- MFA for Parallels RAS
- MFA for Windows and RDP
- MFA for RADIUS
- MFA for OWA
- MFA for VPN
- MFA for ADFS
- MFA for Roundcube
- MFA for Office 365 (SSO)
- MFA for AD, LDAP, Databases
About Us – AFT India | IT Security & Cybersecurity Hardware Solutions
Our Cyber Protection Hardware Products & Solutions

Software Protection USB Dongles
Our Products & Solutions
AFT India offers a broad portfolio of cybersecurity hardware products and solutions, including:
- Cyber Threat & Protection Solutions: Advanced hardware designed to detect, prevent, and neutralize cyber threats.
- Smart Mobile POS Systems: Secure and efficient point-of-sale hardware for modern retail and service environments.
- Multi-Factor Authentication (MFA): Featuring FIDO2 PIN+ Series, Dual-Port FIDO2 Security Keys, PIV Devices, Classic OTP Tokens, and more for enhanced access security.
- FIDO2 Authentication Devices: Including NFC-enabled keys, TOTP-compatible tokens, and programmable authentication tokens.
- Dynamic Strong Password Authentication: Innovative duplication and replication systems enhancing password security.
- Cloud-Based and On-Premise MFA Platforms: Flexible deployment tailored to your IT infrastructure.
- Wi-Fi and SMS-Based Authentication: Strong wireless network security with multi-layer authentication.
- Electronic Visit Verification (EVV): Secure tracking and verification solutions for healthcare and field services.
- Software Protection Dongle Keys: Protect your software assets from unauthorized use.
- MFA Solutions for Multiple Platforms: VPN, Remote Desktop, Exchange, Office 365, IIS Websites, Cloud Services, and more.
Secure your digital future with AFT India — where technology meets trust in cybersecurity hardware.
For inquiries and detailed product information, please contact us via aftindia.in.
If you want, I can help you create additional sections or content for your website. Would you like that?
About Us — Cyber Protection Hardware & IT Security Hardware Solutions
At Aftindia.in, About Us, we design, supply, and support enterprise-grade cybersecurity hardware and IT security hardware products that protect identities, data, and applications. From FIDO security keys and biometric security to software protection dongles and OTP hardware tokens, our mission is to make strong, hardware-backed security simple and reliable for businesses worldwide.
Our mission
About Us – To reduce cyber risk by delivering resilient, standards-based hardware solutions that make authentication, encryption, and licensing stronger, user-friendly, and privacy-preserving. We focus on hardware-first security because physical devices — About Us – when designed and managed correctly — About Us – provide tamper-resistant protection that software alone cannot match.
What we build & supply
Cyber Protection Hardware Solutions
We provide hardened, certified hardware devices and appliances that secure endpoints, servers, and critical infrastructure — including token appliances, secure elements, and tamper-resistant modules.
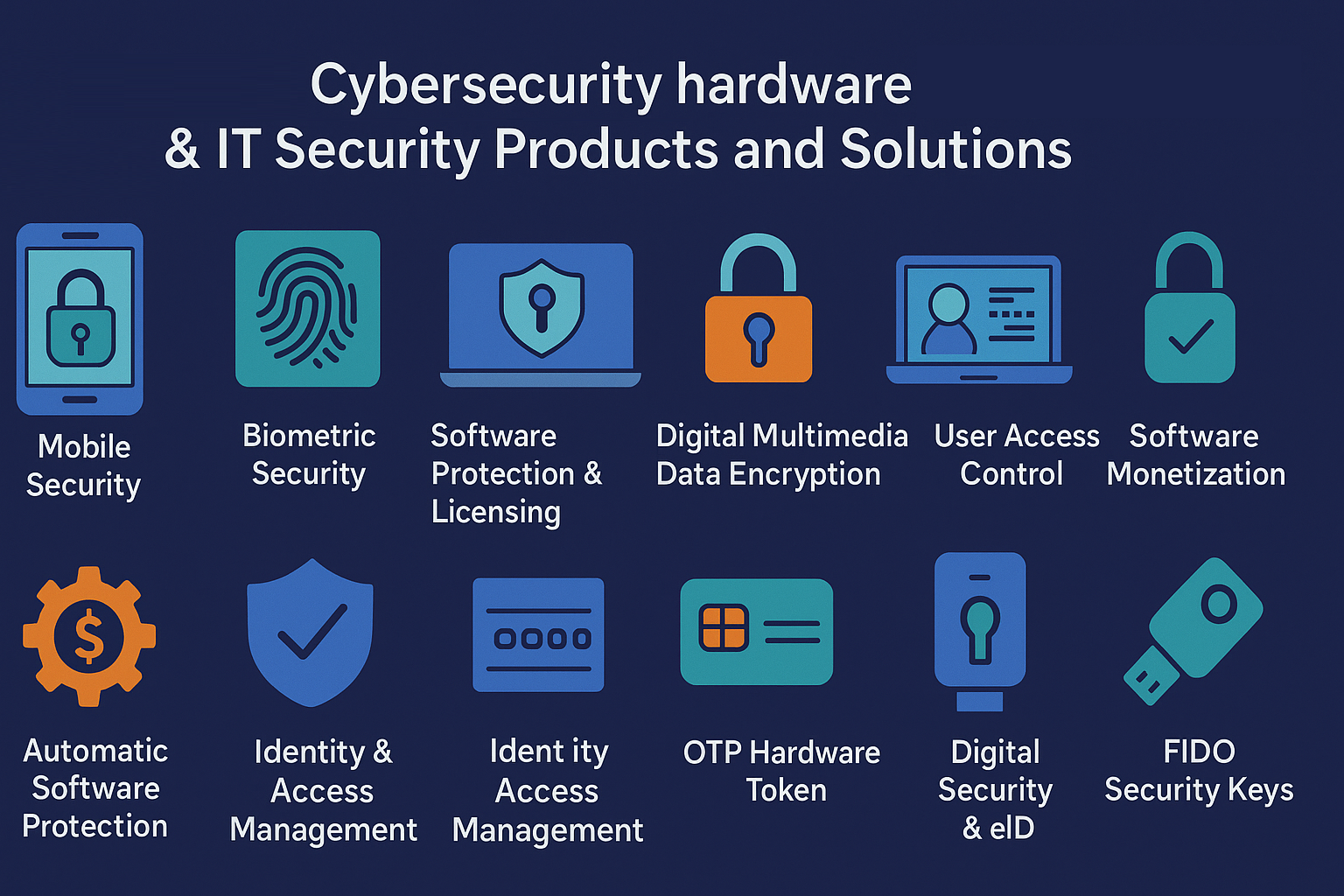
Mobile Security
Secure mobile authentication and contactless tokens (NFC/BLE) for mobile apps, secure payments, and on-the-go access control — supporting modern passwordless flows and mobile PKI.
Biometric Security
Fingerprint and biometric smartcard solutions (match-on-card / on-device biometric verification) that protect privacy by ensuring biometric templates never leave the secure element.
Software Protection, USB HASP Dongle & Licensing
Hardware license dongles and USB license keys for offline/software licensing, anti-piracy and software monetization. Dongles provide tamper-resistant cryptographic key storage and local license checks — ideal for CAD/CAM, industrial, medical, and embedded systems.
Digital Multimedia Data Encryption
Secure multimedia encryption for video, audio, and sensitive content — DRM and containerized encryption that pairs with hardware tokens to enforce playback policies.
User Access Control & Identity & Access Management (IAM)
We integrate hardware authenticators with modern IAM systems to provide zero-trust, least-privilege access controls. Hardware keys and tokens work with SSO, MFA, and identity platforms to secure accounts and administrative access. IAM remains a core strategy for preventing breaches and ensuring the right people access the right resources.
Software Monetization & Automatic Software Protection
Flexible licensing models (subscription, floating, feature flags) are embedded into our hardware protection stacks so ISVs can monetize software reliably and automatically without exposing keys or secrets.
OTP Hardware Token
One-time password (HOTP/TOTP) hardware tokens for offline two-factor authentication and transaction signing — durable, offline-capable devices trusted by enterprises and banking customers.
Digital Security & eID
Secure eID and digital identity issuance solutions (e-ID cards, citizen IDs, employee IDs) using smart cards and PKI to meet regulatory and privacy requirements.
FIDO Security Keys
FIDO-compliant hardware authenticators (FIDO2 / U2F) for phishing-resistant, passwordless authentication. FIDO standards use public key cryptography and device-bound credentials to eliminate passwords and reduce credential theft.
Why hardware-first security
- Tamper-resistant secrets — secure elements and hardware-backed keys keep private keys and biometric templates off the network, reducing theft risk.
- Phishing resistance — FIDO and hardware tokens stop credential phishing because the cryptographic challenge ties to the genuine site.
- Offline & air-gapped capability — hardware solutions enable secure operation where networks are unavailable (industrial controls, labs, remote sites).
- Longevity & compliance — hardware modules simplify compliance with regulations that require secure key management and tamper protection.
Our technology & standards
About Us – We design products to work with open standards and industry best practices: FIDO/WebAuthn for passwordless authentication, ISO smart-card standards for eID, EMV/PCI for payment integrations, and established licensing platforms (Rockey/CL/Sentinel-style approaches) for dongle protection. Adopting standards ensures interoperability and future-proof security.
Industries we serve
Manufacturing, CAD/CAM, healthcare, finance & banking, government & eID, telecom, software vendors (ISVs), and enterprise IT — anywhere strong authentication, content protection, or offline license enforcement matters.
Our approach: secure, private, usable
- Security by design — hardware secure elements, strong crypto, tamper detection.
- Privacy first — biometric templates and keys stay on device whenever possible (match-on-card).
- Seamless UX — frictionless logins (FIDO passkeys, NFC tap), easy card/token issuance for users.
- Flexible deployment — on-prem, cloud-integrated, or hybrid licensing models.
Partnerships & integrations
About Us – We partner with IAM providers, PKI vendors, and leading hardware manufacturers to deliver integrated solutions that plug into existing identity stacks and business processes. We also support custom firmware and SDK integrations for specialized deployments.
Contact / Call to action
About Us – Ready to secure your applications, data, or devices? Contact our solutions team for a consultation, demo, or pilot program.
Email: contact@aftindia.in • Phone: +91 96738 43073 | +91 78751 46441 • Get a demo → [Contact]
Frequently Asked Questions (FAQ)
Q: What is the difference between an OTP hardware token and a FIDO security key?
A: OTP tokens generate one-time passwords (HOTP/TOTP) for login codes, while FIDO security keys use public-key cryptography to provide phishing-resistant, challenge-response authentication and often enable passwordless login. Both have use cases; FIDO is preferred for phishing resistance.
Q: How do software protection dongles help ISVs?
A: Dongles enforce licensing by storing cryptographic keys on a hardware device; the protected software checks the dongle at runtime, enabling offline license enforcement and reducing piracy.
Q: Are biometric templates stored on the cloud?
A: In privacy-preserving deployments we recommend match-on-card or on-device verification so templates never leave the secure hardware. This reduces privacy and regulatory risk.
Q: Do your hardware tokens work with popular IAM platforms?
A: Yes — our hardware authenticators integrate with major IAM and SSO providers to enable MFA, passwordless flows, and device-based access control.
Citations (the most load-bearing factual claims)
- FIDO / FIDO2 standards & phishing resistance.
- Identity & Access Management definition & role in security.
- Software protection dongles definition and use for license enforcement.
- OTP hardware token and OTP explanation.
Healthcare Security Solution
AFTINDIA is the leading supplier of two-factor authentication and smart-card-based security solution and products company, we offer digital authentication and identification solutions to help healthcare organization to access their data on mobile device and PC workstations. Our cloudSign solutions provides electronic document signature service and paperless solution.
Government Security Solution
AFTINDIA offers multiple choices of strong authentication for Governmental and public institutions to enhance their security, reduce paper work and increase efficiency. Our security product portfolio provides high level security for digital document signing , system secure logon, secure two-factor authentication on both desktop and mobile devices, and secure physical access control to avoid unauthorized access and protect confidential resources.
Enterprise Security Solution
AFTINDIA is well positioned to provide enterprise-wide identity and authentication, including hardware, middleware and authentication platform.
Payment Security Solution
From initial payment card issuance to transaction processing requirements, AFTINDIA payment security solutions protect the confidentiality and integrity of transactions. Our transaction security solutions are designed to support the needs of payment processing environments for credit, debit, e-purse and chip cards, internet payment applications, web-based personal identification number (PIN) delivery, and more.
Why Choose About Us Aft India?
✅ Expertise in security & duplication technologies
✅ Reliable, scalable solutions for modern businesses
✅ Customized services to meet project-specific needs
✅ Trusted by professionals across industries
Schedule a free consulting call with a representative
Company Overview
Established in 2009, About Us AFT INDIA is a trusted global service provider of advanced cybersecurity hardware products and solutions. Serving customers across many countries, we operate with head office located in Pune, Maharashtra, India, backed by a highly skilled international team.
With our dedicated professionals—more than half of whom are R&D engineers—AFT INDIA focuses on continuous innovation, investing heavily in research and development to deliver cutting-edge solutions. Our extensive experience and deep understanding of market demands enable us to offer a wide range of certified, patent-backed products designed for performance, reliability, and global compliance.
As a proprietorship company, we are committed to delivering reliable, cost-effective cybersecurity solutions that meet the evolving needs of our customers. We look forward to building a long-term and trusted partnership with you.

Not Sure What About Us Products & Solutions Is Right For Your Company?
About us AFT INDIA – Trusted Cybersecurity Partner Since 2009
About Us Aftindia’s Copy Protection, Software Protection, USB Dongle, Hardware Lock, Licensing Control, Hard Drive Duplicators, HDD/SSD Duplicators, Portable Mini Duplicators, SATA HDD/SSD Duplicators, NVME M.2 PCIe SSD Duplicators, SAS Duplicators, CRU Duplicators, Duplication Replications Solutions, Replication System, Cybersecurity Hardware, Identity Security & Access Management.
Contactless Security Keys, Biometric + Fingerprint Security Keys, FIDO U2F Security Keys, FIDO U2F FIDO2 Security Key Devices and Hardware Passkeys, FIDO2 Security Keys, passwordless login, 2FA/MFA via FIDO/OTP authentication tokens and PKI Token, Flash Duplicators, USB Drive Duplicators, USB 2.0 Duplicators, USB 3.0 Duplicators, SD & MicroSD Duplicators, CF/CFast Duplicators, SATA DOM Duplicator, CD/DVD Duplicator products and solutions for protecting cloud, data, and software and securing digital content.

